INTRODUCTION:-
Anyone who's been in the financial world for any length of time knows how fast that world is changing. Years ago, 'balancing the books' literally involved poring through books and ledgers. Today's business world is much more complex-we not only have databases and software, but multi-national companies worth billions of dollars.
Now days we can say 'There are two type of companies in which fraud happening another who don't know that fraud is happening'
Today's villain are using mouse and keyboard instead of using mask and gun when we are gone in digital world.
What was the use of fingerprint in 19th century DNA analysis for the 20th century, forensic accounting and forensic auditing will be for 21st century.
'This term has not been defined anywhere. However, since the object is to relate the findings of audit by gathering legally tenable evidence and in doing so the corporate veil may be lifted (in case of corporate entities) to identify the fraud and the person responsible for it (a criminal offence).'
The concept of Financial Auditing may be defined as 'a concentrated audit of all the transactions of the entity to find the correctness of such transactions and to report whether or not any financial benefit has been attained by way of presenting an unreal picture'.
Characteristics and skills of forensic auditor:-
General Skills for Forensic Audit
(a) Knowledge of entity's business and legal environment.
(b) Awareness of computer assisted audit procedures.
(c) Innovative approach and skeptic of routine audit practices.
Areas of Specialty Needed
(a) Financial Statement misrepresentations
(b) Economic damages calculations
(c) Fraud prevention, detection and response
(d) Valuation
(e) Bankruptcy, insolvency and reorganization
(f) Family law
(g) Computer forensic analysis
Essential Traits and Characteristics
(a) Analytical
(b) Detail-oriented
(c) Ethical
(d) Effective oral communicator
(e) Responsive
(f) Insightful
(g) Inquisitive
(h) Intuitive
(I) Persistent
(j) Skepticism
(k) Evaluative
(l) Function well under pressure
(m) Generate new ideas and scenarios
(n) Confident
(o) Makes people feel at ease
(p) Team player
(q) Adaptive
Core Skills
- Simplify the information
- Critical/strategic thinker
- Identify key issues
- Auditing skills
- Investigative ability
- Effective written communicator
- Investigative intuitiveness
- Synthesize results of discovery and analysis
- Think like the wrongdoer
- Understand the goals of a case
- Tell the story
- See the big picture
- Organize an unstructured situation
- Solve unstructured problems
Fraud Cases discussion:-
The global economy makes it possible for an investor in New Delhi to electronically manage his stock portfolio in New York. It allows an entrepreneur in Jersey to run a business in Jakarta.
Globalization has been a boon to businesses around the world but it has also created endless opportunities for bad guys willing to exploit weaknesses in internal controls.
These days, the Internet is as much a conduit for crime as it is for commerce. It enables crimes as diverse as drug trafficking, corporate fraud, and terrorism to jump from Syria to San Diego with the click of a mouse. It opens up new possibilities for mobsters, computer hackers, spies, and terrorists.
(Case-1) 5 engineering students dupe bank of Rs 8.6 crores using e-wallet
(KOLKATA: INDIA) A group of five engineering students
has robbed a bank of crores by using fake mobile wallet transactions over the four
months (as on 21st march 2016). Though all of them, along with four others, have
landed in police net, the cops are worried over the alarming trend of youngsters
exploiting tech loopholes to dupe customers and banks alike.
A private sector bank, which had opened its wallet transaction operations in December,
did not realize that there was a basic flaw in their system. If a customer tried
to pay from his own wallet to another wallet holder and the latter knowingly or
unknowingly had his internet connection switched off the one who is transferring
the amount did not end up losing any money. Instead, it was the bank that ended
up paying for him. The bank did not realize the fraud till Rs 8.6 crore was siphoned
off.

(CASE-2) - ATM Fraud - Case Study of a Commercial Bank in Pakistan
ATM occupies an important position in the e-Banking portfolio. It has given the consumers a quality of life allowing them to access cash and other financial information. Its role in promoting, developing and expanding the concept of 'Anytime Anywhere Anyplace' banking is undeniable. It offers a real convenience to those who are on the run in their everyday life, but at the same time, it also carries a big element of risk.
In this case the banks' internal control system had failed to detect the implantation of mapping bug which deprived the bank of more than 21 million Pakistani Rupees. In addition, lack of understanding of higher management on the systems & procedures supporting ATM Infrastructure played a significant role in developing the bug.
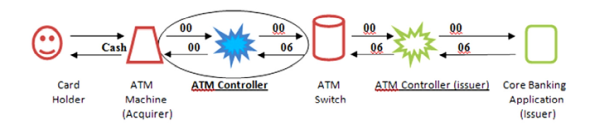
The ATM Controller famously known as Transaction Processing Switching or Financial Middleware is one of the most important components in conducting electronic transactions. The first ATM Controller was introduced in Pakistan by TPS Pvt. Limited in 1996.
In Pakistan, the ATM transactions are based on predefined and pre-allocated mapping codes ranging from 00 to 99 wherein '00' code has been reserved for 'cash withdrawal' by all the banks. Accordingly, the ATMs and the associated ATM Controllers have been configured on the parameters that does not allow 'cash withdrawal' from ATM if any other code except for the '00' is received from the issuer bank's core banking application. ATMs are always attached with ATM Controller when conducting inter-bank transactions involving two different banks. Once the card holder of Bank-A (issuer bank) access the ATM of Bank-B (acquirer bank), the ATM of Bank-B sends the card holder credentials to Bank-A for verification and authorization. This communication is conducted through the ATM controller deployed at both Bank-A and Bank-B. After receiving the authorization from issuer bank i.e. Bank-A, the ATM of acquirer bank i.e. Bank-B disburses the cash to cardholder of Bank-A.
In this case study, investigated that the presence of a mapping bug when the ATMs of ACB Bank Limited started disbursing cash to the card holders of Bank-A having 'zero' or 'insufficient' balance in their bank account. Despite of the fact that the Bank-A sent a rejection '06' code from its ATM controller to ACB Bank ATM Controller, but due to the presence of a mapping bug, the ATM Controller of ACB Bank started reading every code as ''00' and disbursed the cash as depicted in the following diagram:
(Case -3) Syndicate Bank writes off Rs 883 crore against fraud
Syndicate Bank on Tuesday 17 may 2016 said that it wrote off Rs.882.64 crore in the fourth quarter (the three months ended 31 March) because of fraud at its branches in Jaipur over the last four years.
The bank did this after it found out that a few hundred accounts had been opened, and loans of a few crore rupees given to each on the basis of fraudulent documents, such as fake or non-existent cheques, letters of credit and insurance policies.
According to a senior official at Syndicate Bank, the lender detected some signs of a fraud during the audit of its October-December quarter results that took place in January.
'More than 350 accounts were opened with these branches and loans worth Rs.2-2.5 crore each were availed using fake documents. The amounts were so small that fraud management systems could not detect them'.
(Case 4) Corporate Accounting Scandal at Satyam Computer Services Limited: A Case Study of India's Enron
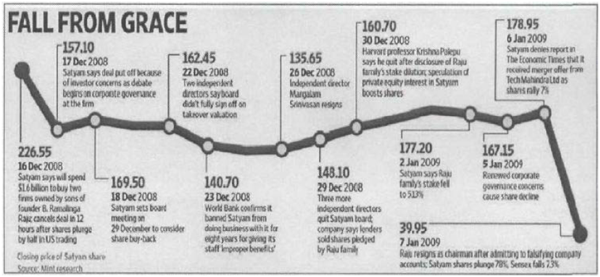
Ironically, Satyam means 'truth' in the ancient Indian language 'Sanskrit'. Satyam won the 'Golden Pea- cock Award' for the best governed company in 2007 and in 2009.
Unfortunately, less than five months after winning the Global Peacock Award, Satyam became the centerpiece of a 'massive' accounting fraud.
Mr. Ramalinga Raju (Chairman and Founder of Satyam; henceforth called 'Raju'), who has been arrested and has confessed to a $1.47 billion (or Rs. 7800 crore) fraud, admitted that he had made up profits for years. According to reports, Raju and his brother, B. Rama Raju, who was the Managing Director, 'hid the deception from the company's board, senior managers, and auditors'. The case of Satyam's account- ing fraud has been dubbed as 'India's Enron'.
Satyam Computer Services Limited was a 'rising-star' in the Indian 'outsourced' IT-services industry. The com- pany was formed in 1987 in Hyderabad (India) by Mr. Ramalinga Raju. The firm began with 20 employees and grew rapidly as a 'global' business. It offered IT and business process outsourcing services spanning various sectors. Satyam was as an example of 'India's growing success'.
From 2003-2008, in nearly all financial metrics of in- terest to investors, the company grew measurably. Sat- yam generated USD $467 million in total sales. By March 2008, the company had grown to USD $2.1 bil- lion. The company demonstrated 'an annual compound growth rate of 35% over that period'. Operating profits averaged 21%. Earnings per share similarly grew, from $0.12 to $0.62, at a compound annual growth rate of 40%. Over the same period (2003‐2009), the company was trading at an average trailing EBITDA multiple of 15.36. Finally, beginning in January 2003, at a share price of 138.08 INR, Satyam's stock would peak at 526.25 INR-a 300% improvement in share price after nearly five years. Satyam clearly generated significant corporate growth and shareholder value.
In April, 2008 Satyam became the first Indian company to publish IFRS audited financials. On December 16, 2008, the Satyam board, including its five independent directors had approved the founder's proposal to buy the stake in Maytas Infrastructure and all of Maytas Properties, which were owned by family members of Satyam's Chairman, Ramalinga Raju, as fully owned subsidiary for $1.6 billion. Without shareholder approval, the directors went ahead with the management's decision. The decision of acquisition was, however, reversed twelve hours after investors sold Satyam's stock and threatened action against the management. This was followed by the law-suits filed in the US contesting Maytas deal. The World Bank banned Satyam from conducting business for 8 years due to inappropriate payments to staff and inability to provide information sought on invoices. Four independent directors quit the Satyam board and SEBI ordered promoters to disclose pledged shares to stock exchange.
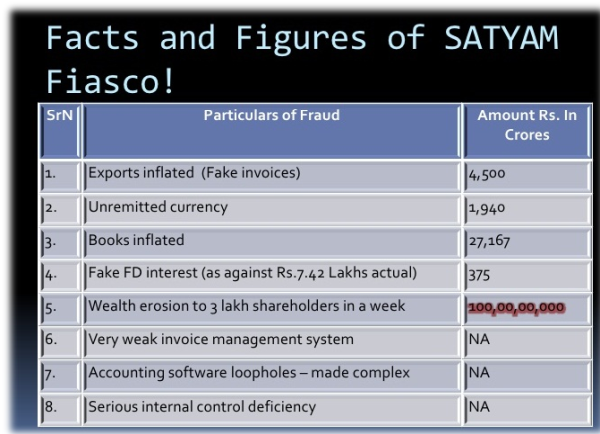
On January 7, 2009, Mr. Raju disclosed in a letter to Satyam Computers Limited Board of Di- rectors that 'he had been manipulating the company's accounting numbers for years'. Mr. Raju claimed that he overstated assets on Satyam's balance sheet by $1.47 billion. Nearly $1.04 billion in bank loans and cash that the company claimed to own was non-existent. Satyam also underreported liabilities on its balance sheet. Satyam overstated income nearly every quarter over the course of several years in order to meet analyst expectations. For example, the results announced on October 17, 2009 overstated quarterly revenues by 75 percent and profits by 97 percent. Mr. Raju and the company's global head of internal audit used a number of different techniques to perpetrate the fraud. 'Using his personal computer, Mr. Raju created numerous bank statements to advance the fraud. Mr. Raju falsified the bank accounts to inflate the balance sheet with balances that did not exist. He inflated the income statement by claiming interest income from the fake bank accounts. Mr. Raju also revealed that he created 6000 fake salary accounts over the past few years and appropriated the money after the company deposited it. The company's global head of internal audit created fake customer identities and generated fake invoices against their names to inflate revenue. The global head of internal audit also forged board resolutions and illegally obtained loans for the company'. It also appeared that the cash that the company raised through American Depository Receipts in the United States never made it to the balance sheets.
Global auditing firm, PricewaterhouseCoopers (PwC), audited Satyam's books from June 2000 until the discovery of the fraud in 2009. Several commentators criticized PwC harshly for failing to detect the fraud. Indeed, PwC signed Satyam's financial statements and was responsible for the numbers under the Indian law.
(Case-5) Email Fraud Techniques
Many types of fraud exist, and email is an inexpensive and popular method for distributing fraudulent messages to potential victims. Approximately 90% of all email sent worldwide are spam, spoof and phishing.
Several attempts have been made to obtain payments from users of IATA (International air transportation association) products and services. The most common technique is through the use of fraudulent emails, with or without fake invoices attached. Additionally, some attachments to fraudulent emails have been found to contain malware.
|
Recent examples of fraudulent e-mail issued by IATA. |
|
*ONGC fraud case is a good example in context with India
Techniques used for forensic audit
- Off balance sheet item
- Critical point auditing
- Propriety audit
- Analysis technique-
- Proactive method -excel, advance excel, digital analysis Bedford's law etc
- Reactive methods-interpersonal communication skills are the basic thing which a forensic auditor required - communication with whistle blower.
Recent development in forensic audit
- Insurance claims investigation
- Divorce and matrimonial proceeds between companies
- White Color crime investigation (e.g. SATAYM)
- Share holder dispute
- Forensic audit in business valuation concerning frauds to finance
Application of relevant section of Companies acts 2013 and SAS in forensic audit
1. Section-211 and 212 of companies act 2013 related with SFIO (SERIOS FRAUD INVESTIGATION OFFICE), requires reporting and investigating in fraud with the help of CID, CBI and police department. More than 800 cases filed Satyam was one of them.
2. Another section 143(12) says if an auditor in the course of his or her audit reason to believe that an offence involving fraud has been committed against the company by companies officer of employee than have to immediately report to the central Government within prescribed time.
3. SA-240: This is a specific auditing and assurance standard pronounced by the ICAI (effective from April 1, 2009), relating to an auditor's duty as regards fraud and error in financial statements. This standard states that the primary responsibility for the prevention and detection of fraud and error rests, with both: 1) those charged with governance and 2) the management of an entity. The standard also spelt out the auditor's enhanced responsibility and laid down expectations of a far more penetrative audit than ever before in the past.
4. SA-505: Some of the relevant provisions of 'Audit Evidence' given by SA 505 provide some insight into the procedure of weighing and judging evidence. The relevant provisions are:
External evidence is usually more reliable than
internal evidence.
Internal evidence is more reliable when internal controls are satisfactory.
Written or documented evidence is more reliable than oral representations.
Evidence obtained by the auditor is more reliable than that obtained through the
Auditee.
According to the Nyaya Shastra there are several aids called pramanas or types of proofs which can facilitate reaching the truth.
Pratyaksha:
Anything physically verifiable.
Anumana: Inference
Upamana: Description
Shabda: Axioms or undisputed theories
Arthapat: Conclusion through the principle of Reductio Ad
Absurdum
Anupalabdhi: Conclusion through absence of truth
5. CARO clearly spells out the duty of fraud towards fraud detection and reporting. In the recent past, an auditor's duty towards fraud detection was further accentuated by the High Court in judgment -
Sales Tax Practitioners' Association (STPA) of Maharashtra v/s the State of Maharashtra
In the wake of Enron, WorldCom, and other scandals, companies started paying more attention to the risks of fraud and have hired many forensic accountants. And thanks to standard on auditing, Sarbanes-Oxley, and the collapse of Arthur Andersen, auditing groups have been working more closely with their forensic accounting counterparts; often this means they are throwing more work at you.
Popular methods of Prevention, detection and correction of fraud & control in forensic auditing:-
- Training minimum 200 times in a year which is minimum no. of working days in a year, Messages all over organization related to awareness.
- Is there Password sharing in organization? If yes there should be control over sharing and changing password.
- IP address monitoring
- Mac address Monitoring -many accounting software are not capable to detect Mac address. Even Finacle and oracle finance are not able to detect ,SAP providing with some extent but not fully capable.
- Continuous vigilance and intelligence gathering are two items helps in prevention of fraud in banking industry.
Three methods
1- Benfords law -we know law of probability where every digit has actual chance of appearance but according to Bedford's law , probability is wrong for the purpose of fraud detection.
LAW-30% record start with digit 1 if more than 30 % there may be fictitious sale
Condition -
- Minimum no of records should be 1000 and only numerical field
- There should be no control over the record E.g. sale invoice data can be used if there is no control
- Alphanumeric data can't be use for this method
2- Relative size factor- It is based on assumption that high value have already pressure and more chances of detection. It is like ledger scrutiny but slightly different where we have to select the invoice which is varying from other with considering fact that lower amount have more chances of fraud.
3- Beneish model- it is very popular model for fraud detection which is also used by World Bank and taught to management students of top universities of the world like Chicago, Indiana University. This model gives M-score formula and result of formula decides whether there is fraud possibility of not. If result
- More than (-2.22) high fraud existence possibility
- Less than (-2.22) no fraud possibility
Success rate of this model is 76%.
Merrill lynch, prudential securities used this model.
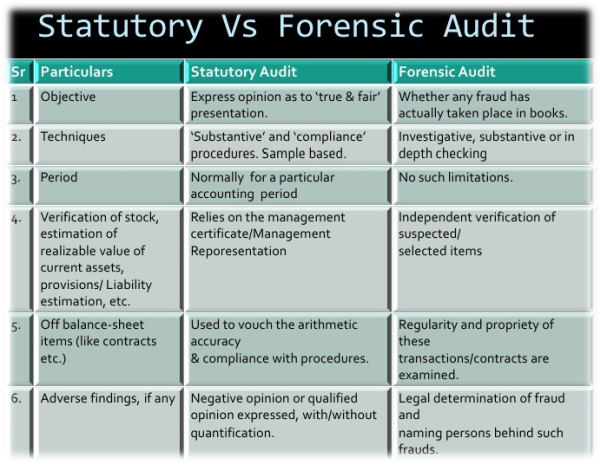
Difference between statutory and Forensic audit-
Conclusion:
From Enron, WorldCom and Satyam, it appears that corporate accounting fraud is a major problem that is increasing both in its frequency and severity. Research evidence has shown that growing number of frauds have undermined the integrity of financial reports, contributed to substantial economic losses, and eroded investors' confidence regarding the usefulness and reliability of financial statements. The increasing rate of white-collar crimes demands stiff penalties, exemplary punishments, and effective enforcement of law with the right spirit.
We are the first line of defense against fraud. We are the beat cops not just checking boxes, but actually conducting surveillance, and constantly scanning the horizon for irregularities.
We need to keep being proactive. Keep your independence. Keep asking the tough questions. Keep raising the red flags. When you think about it, conducting an ethical audit of a company is just as vital as arresting a corrupt CEO.
Forensic auditing combines legalities alongside the techniques of propriety (VFM audit), regularity, investigative, and financial audits. The main aim is to find out whether or not true business value has been reflected in the financial statements and whether any fraud has taken place.
Source:
- ICAI study material for certificate course of forensic audit
- Times of India dated 12/10/2017
- India Today (Delhi) June 15,2016
- Live Mint July 29,2016
- IATA - Warning documents.
- International Journal of Business and Management; Vol. 7, No. 22; 2016
- ACRN Oxford Journal of Finance and Risk Perspective
- (Special Issue of Finance Risk and Accounting Perspectives, Vol.5 Issue 1, March 2016, Page 230-238)
- S.VASUDEWAN article ( the chartered accountants journal)








 CAclubindia
CAclubindia
